geef aandacht aan je wachtword en verander ze.
back up op papier en in je keychain, geef master password aan je safari chrome off Firefox.

To better protect our users’ websites, we work with a lot of data from sources like our Security Services Team and the Wordfence network. We try to understand not just what attackers are doing, but also how and why. Our research into a recent campaign revealed an interesting method of attack, and contributed to the development of a new feature.
Password Leaks Are a Rich Source of Information for Hackers
During the last several years, hackers have compromised a wide range of organizations and harvested account details from them. The details almost always include usernames or email addresses, along with hashed versions of passwords (or even worse, plain-text passwords). These compromised accounts are often bought and sold on the dark web, but occasionally they’re also leaked publicly.
For hackers, the value of a stolen user account goes well beyond being able to log in to the compromised website. Hackers are well aware that people are unlikely to use best practices when it comes to password management. In other words, they’re likely to use weak passwords and to repeat the same passwords across multiple accounts. So the hackers try to explore every account they may be able to hijack with a given username and password.
As we’ve discussed before, hackers can do a lot with a hijacked website.
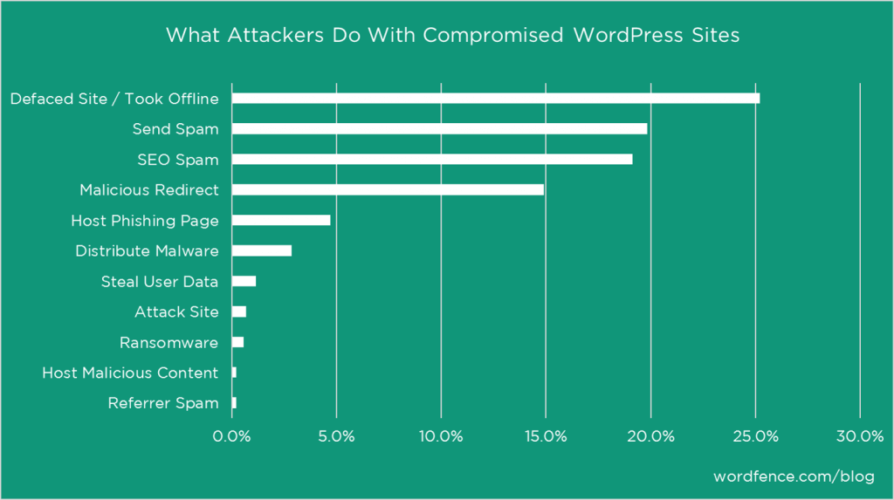 We wrote that post two years ago, but all of those criminal activities are still going on today, with the new addition of cryptojacking attacks. WordPress websites are still attractive targets for hackers.
We wrote that post two years ago, but all of those criminal activities are still going on today, with the new addition of cryptojacking attacks. WordPress websites are still attractive targets for hackers.
Leaked Accounts Used in Malware Campaigns
We observed a few interesting techniques hackers have been using with leaked accounts during the last several weeks. Normally, they would face several obstacles when trying to take over a WordPress website’s administrator account:
- They don’t know the administrator username
- They don’t know the password
- They fail too many times to log in, so they get blocked by plugins, servers, or networks
But the leaks have helped some attackers overcome these obstacles and find valid accounts on a lot of WordPress sites. Imagine that Bob Smith runs a WordPress site at example.com. If he used bob.smith@example.com as his primary email address at a website whose accounts were leaked, his details in the leak would look something like this:
bob.smith@example.com:pony123
This yields several pieces of information for hackers to use: Bob’s email address, some likely usernames, and a password he uses (pony123). Some published leaks combined data from several other leaks, yielding two or more accounts that probably belong to the same person. If Bob used his Gmail account at another compromised site, then the leak might look like this:
bob.smith@example.com:pony123
bob@gmail.com:pony123456

Finding WordPress Sites in the Leaks
It seems that hackers are using a direct approach to find WordPress sites among the leaked accounts. In our example, they simply check example.com to see if it’s running WordPress. But they also seem to be following redirects: in a case where example.com redirects to example2.com, these login attempts were being made against example2.com even though it never appeared in the leaks.
We observed an interesting twist, though: sometimes email addresses on completely unrelated domains (like Gmail) were being used during login attempts. In this example, we observe bob@gmail.com and pony123456 being attempted on example.com. How did the hackers know to try it? It’s unlikely they actually got into the Gmail account and found emails from WordPress there; if they had, they could have simply used the “reset password” feature to take over the site. Instead, in the cases we observed, the email address was actually publicly used as a contact address in the site’s DNS registration. In other words, Bob used bob@gmail.com when he registered example.com. So the hackers may be searching DNS records for leaked email addresses to find target sites.
Getting Valid Usernames From the Leaks
The attackers behind the most recent campaign use email addresses to create a small set of usernames that are likely to be real administrator users on target sites. First they try “admin” since it’s the default username, and presumably the most common. Then they also try the full email address (like bob.smith@example.com), and then a couple of variations on the first part of the email address: one with all dots removed (bobsmith) and another with anything before the first dot (bob). Altogether, they only try to log in four times. The leaked accounts give them a much higher chance of success than brute-force attacks or guessing common passwords, while keeping the number of failures small enough that they don’t get blocked.
Leaks Being Used
We have copies of public leaks, so we’ve been able to locate the source of some of the compromised credentials used in the attacks. Many of them came from the set of 1.4 billion accounts leaked in December (which includes several previous leaks). Of the rest, every single one we checked was listed in at least one leak on HaveIBeenPwned. This demonstrates the tenacity of the attackers, and the way they can find value even in seemingly unrelated breaches.
What We’ve Done to Address This
Because of the small number of login attempts these attackers make, standard brute force login protection is not enough to block these kinds of attacks. Currently has two additional features that can have an effect in stopping this attack: Two Factor Authentication and “Immediately lock out invalid usernames.” But we decided we needed a more robust tool to deal with these kinds of attacks thoroughly.